
ESUP-OTP et CAS 6.4
ESUP-Days #32 | 28 Sept. 2021
- Aymar Anli - Université Paris 1 Panthéon-Sorbonne
- Vincent Bonamy - Université de Rouen Normandie

 ESUP-OTP est sur le github ESUP ! :
ESUP-OTP est sur le github ESUP ! :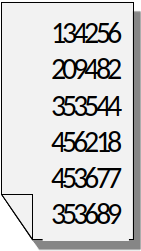 Codes à imprimer
Codes à imprimer
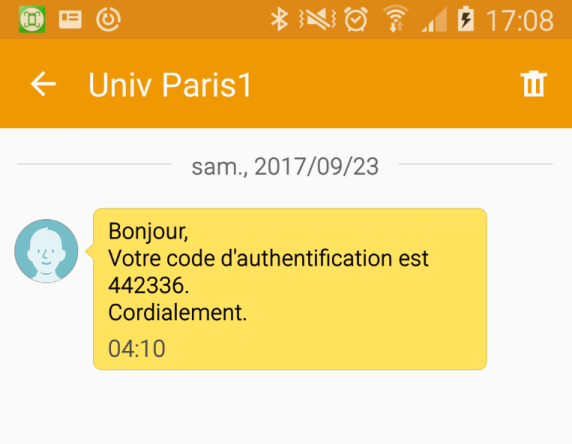 SMS/Mail
SMS/Mail
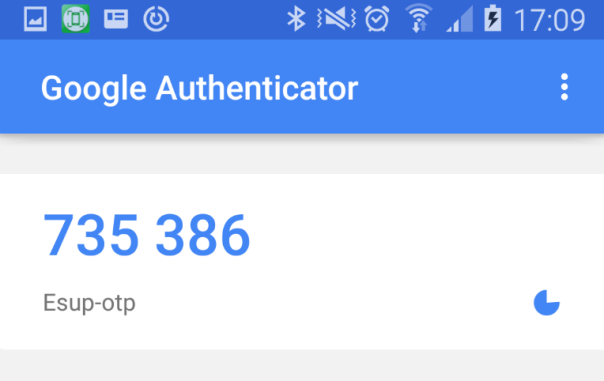 TOTP w/ Google Auth
TOTP w/ Google Auth
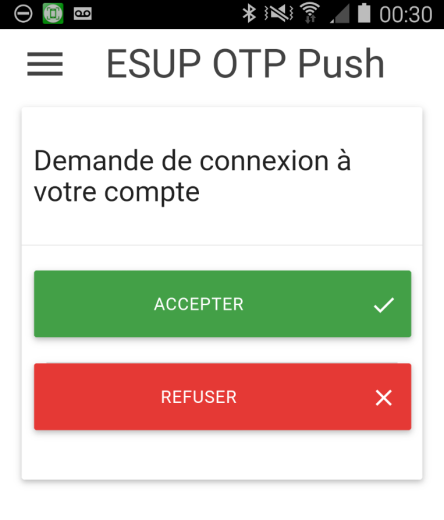 Notification mobile
Notification mobile
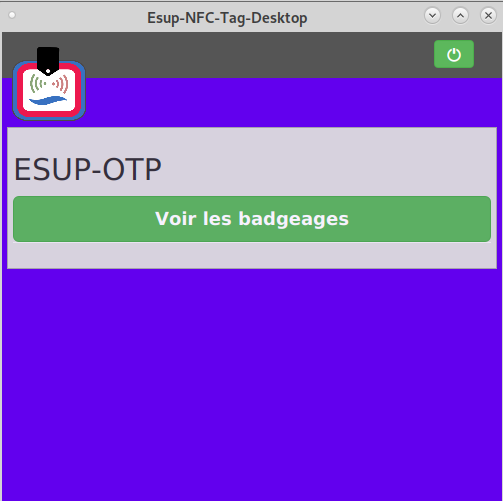 Badgeage NFC
Badgeage NFC
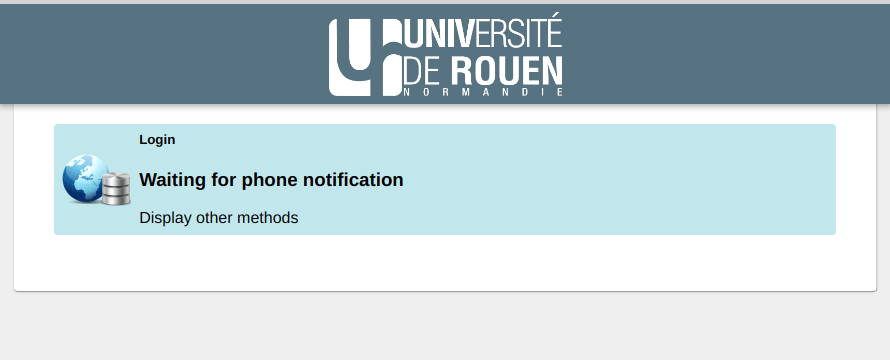 En attente de validation mobile : notification ou badgeage NFC
En attente de validation mobile : notification ou badgeage NFC
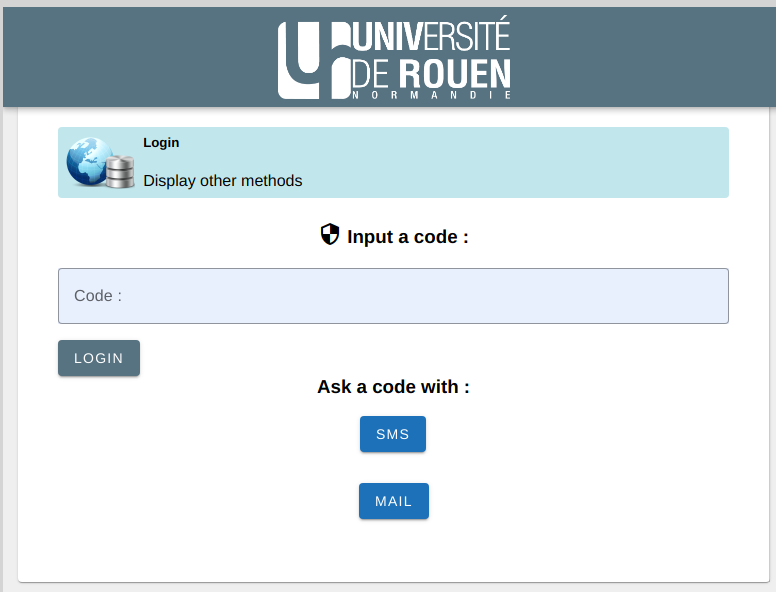 ... ou entrée d'un code
... ou entrée d'un code 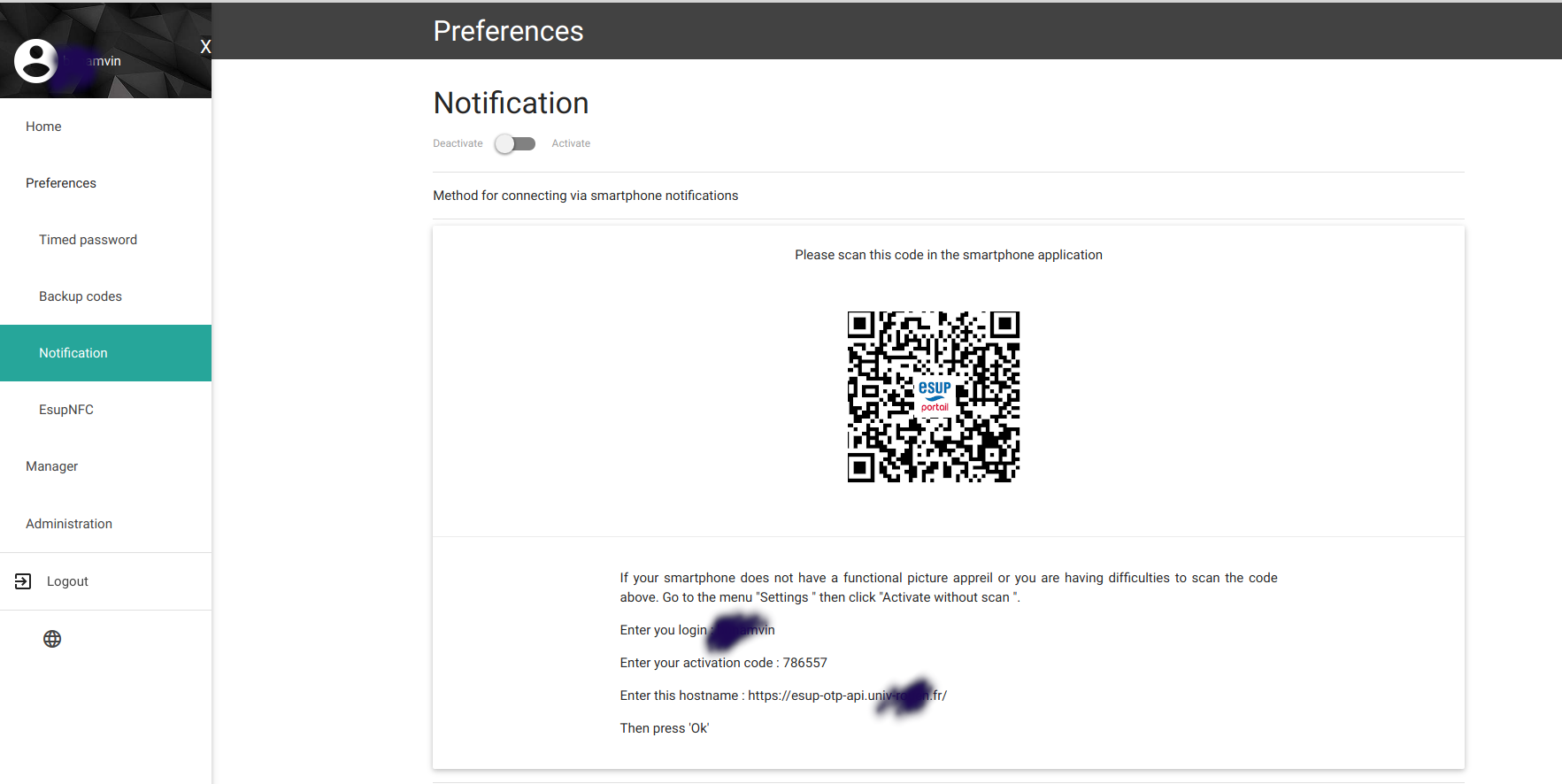 ESUP-OTP enrôlement avec le QR-Code
ESUP-OTP enrôlement avec le QR-Code
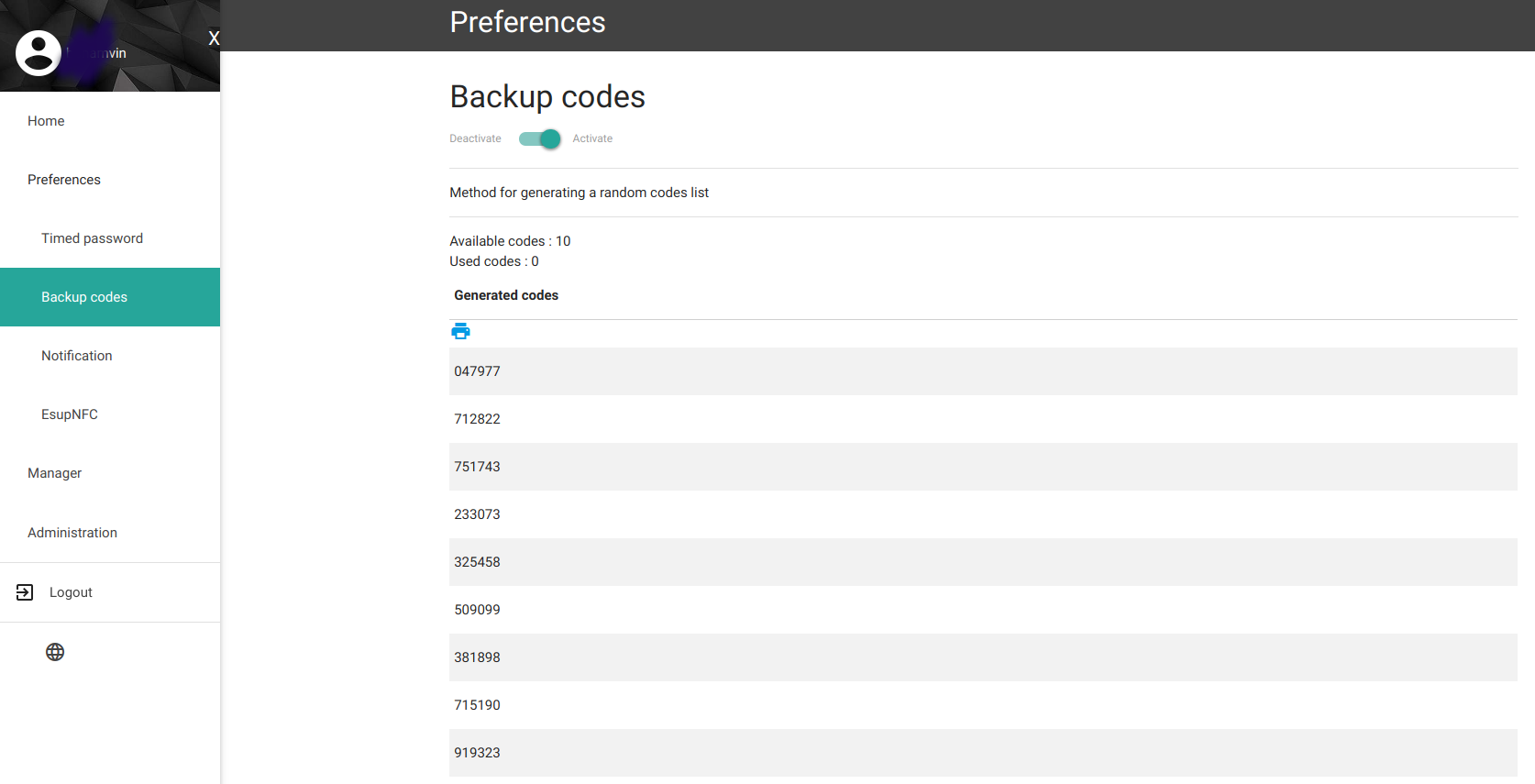 ESUP-OTP codes de secours
ESUP-OTP codes de secours
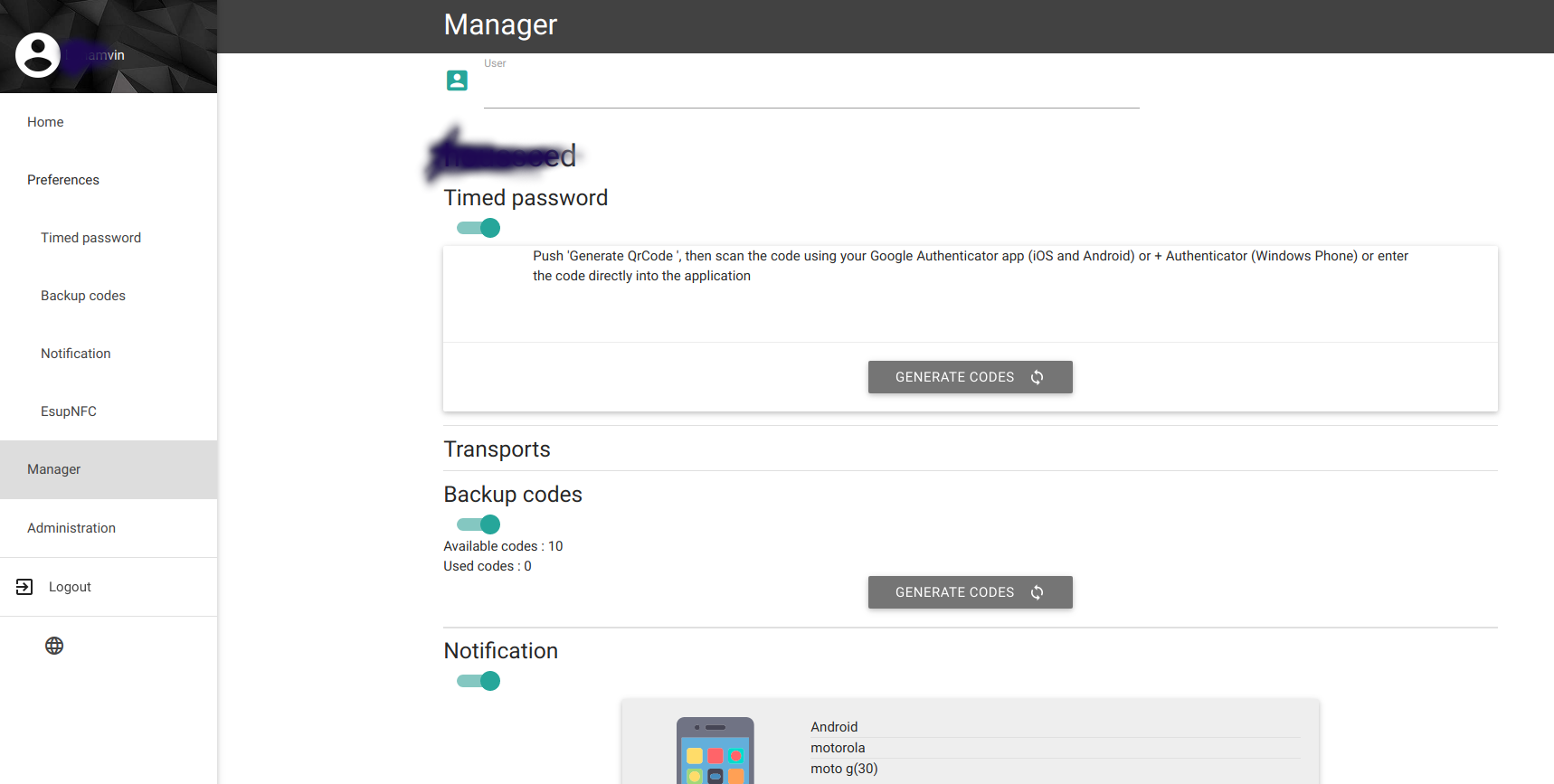 ESUP-OTP Manager Interface
ESUP-OTP Manager Interface
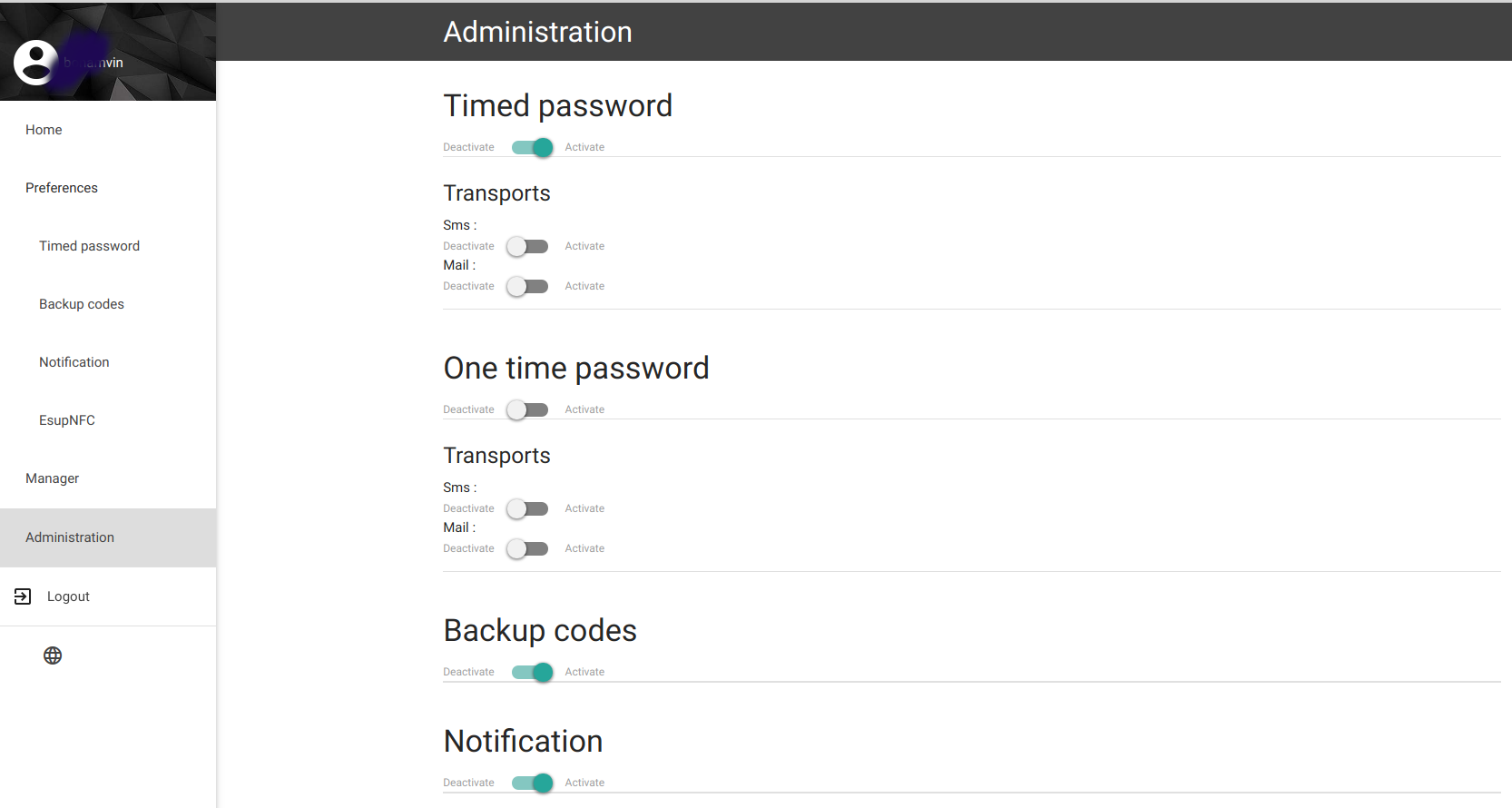 Permet d'activer/désactiver les possibilités de MFA proposées par ESUP-OTP
Permet d'activer/désactiver les possibilités de MFA proposées par ESUP-OTP 





 Application mobile ESUP AUTH
Application mobile ESUP AUTH
 Applications ESUP-SMSU
Optionnel
Applications ESUP-SMSU
Optionnel
 Applications ESUP-NFC
Optionnel ;-)
Applications ESUP-NFC
Optionnel ;-)
 CF README(s) sur github ESUP
CF README(s) sur github ESUP
git clone https://github.com/EsupPortail/esup-otp-api.git
npm install
# change the fields values in properties/esup.json
npm start
git clone https://github.com/EsupPortail/esup-otp-manager.git
npm install
# change the fields values in properties/esup.json
npm start
...
repositories {
...
maven {
url "https://jitpack.io"
}
}
...
dependencies {
...
implementation "com.github.EsupPortail:esup-otp-cas:3f5de8b7b2"
}
esupotp.rank=0
esupotp.urlApi=https://esup-otp-api.univ-ville.fr
esupotp.usersSecret=changeit
esupotp.apiPassword=changeit
esupotp.byPassIfNoEsupOtpMethodIsActive=true
esupotp.trustedDeviceEnabled=true
esupotp.isDeviceRegistrationRequired=false
...
After=network.target
[Service]
Type=simple
User=tomcat
WorkingDirectory=/opt/esup-otp-api
ExecStart=/bin/npm start
...
...
ServerName esup-otp-manager.univ-ville.fr
...
RequestHeader set X-Forwarded-Proto https
RequestHeader set X-Forwarded-Port 443
RewriteEngine On
RewriteCond %{QUERY_STRING} transport=websocket [NC]
RewriteRule /(.*) ws://127.0.0.1:4000/$1 [P]
<Location />
ProxyPass http://127.0.0.1:4000/ retry=1
ProxyPassReverse http://127.0.0.1:4000/
</Location>
...
cas.authn.mfa.globalProviderId=mfa-esupotp
cas.authn.mfa.groovy-script.location=file:/etc/cas/config/mfaGroovyTrigger.groovy
import java.util.*
import groovy.transform.CompileStatic
class SampleGroovyEventResolver {
def String run(final Object... args) {
def service = args[0]
def registeredService = args[1]
def authentication = args[2]
def httpRequest = args[3]
def logger = args[4]
def mobile = authentication.principal.attributes.mobile
def memberOf = authentication.principal.attributes.memberOf
logger.info("ip : [{}]", httpRequest.getRemoteAddr())
logger.info("mobile : [{}]", mobile)
logger.info("memberOf : [{}]", memberOf)
logger.warn("registeredService.id : [{}]", registeredService.id)
// 10, 11, 12 et 13 sont des ids de services (définis par exemple dans la config CAS via du json)
if ((int)registeredService.id in [10, 11, 12, 13]) && !httpRequest.getRemoteAddr().startsWith("192.168.")) {
return "mfa-esupotp"
}
return null
}
}
dependencies {
...
implementation "org.apereo.cas:cas-server-support-trusted-mfa:${casServerVersion}"
implementation "org.apereo.cas:cas-server-support-trusted-mfa-mongo:${casServerVersion}"
}
cas.authn.mfa.trusted.mongo.clientUri=mongodb://localhost/cas-mongo-database
cas.authn.mfa.trusted.deviceRegistrationEnabled=true
cas.authn.mfa.trusted.expiration=7
cas.authn.mfa.trusted.timeUnit=DAYS
MFA et 2FA dans l’IdP Shibboleth, le serveur CAS d’Apereo et les Fédérations
JRES 2019 [G. Rousse & L. Auxepaules]
shibcas.entityIdLocation=embed
idp.session.enabled = false
{
"@class" : "org.apereo.cas.services.RegexRegisteredService",
"serviceId": "^http://idp\\.univ-ville\\.fr/idp/Authn/External\\?conversation=[a-z0-9]*&entityId=https://mon-sp-sensible\\.univ-ville\\.fr",
...
Attention à bien prendre une version de shib-cas-authn
incluant le PR #3